Cheat Engine (CE) has been a powerful tool for game hacking since its inception in the early 2000s. Its core functionality revolves around memory scanning and manipulation, allowing users to modify values like health, ammo, and currency in real-time.
Older games memory structures were relatively easy to scan and manipulate using user-level tools like Cheat Engine.
Games load data such as health, score, ammo, and currency into memory during runtime. These values are stored at specific addresses and updated as the game progresses.
For example:
- Health might be stored as a
floatorintat address0x00AB1240 - Ammo might be stored as a
4-byte integerat address0x00AC8820
Cheat Engine reads the memory of the target process (via Windows API calls like OpenProcess and ReadProcessMemory) and looks for values that match what the user inputs.
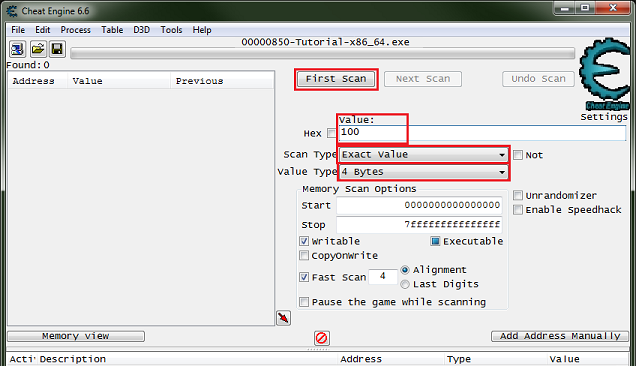
The process was:
- Attach to Process. The user searches for the target process.
- Initial Scan: The user enters a known value (e.g., 100 health or 3 lives), and scans memory for all instances of that value.
- Narrow Down: The user changes the value in-game (e.g., gets hit and health becomes 80) and scans again for the new value in the previous addresses.
- Identify Address: Repeat until a single memory address is found.
- Modify: The user changes the value directly (e.g., set health to 99999).
- Freeze (optional): CE can continuously write the fix value (freeze).
It also included a disassembler and debugger that allowed advanced users to:
- Inject custom assembly code (e.g., overwrite an instruction to always set health to max)
- NOP (No Operation) critical instructions (e.g., skip damage application)
- Hook functions or overwrite them to call user-defined behavior
nop operation (coded 90 in hex) in x86 assembly is just 1 byte. We need to replace the 3 bytes (29 41 08) of the original code with 3 NOPs
// Original code
sub [ecx+0x08], eax ; subtract damage
// Hacked code
nop
nop
nop ; disables the damage completelyModern games use various techniques to prevent memory tampering:
- Address randomization (ASLR)
- Dynamic memory allocation
- Encrypted or obfuscated memory
- Anti-debugging tricks
- Kernel-mode anti-cheat software (e.g., Easy Anti-Cheat, BattleEye)
These protections either make scanning ineffective or flag such actions as malicious.
Cheat Engine was highly effective for hacking older games because of how simply those games handled memory. With no protections in place, even novice users could tweak values and inject code with ease. As game development matured and security tightened, such tools became less effective—but the fundamentals of memory scanning and reverse engineering remain important in game development, debugging, and cybersecurity education.

